Trusted by 500,000+ Professionals Worldwide





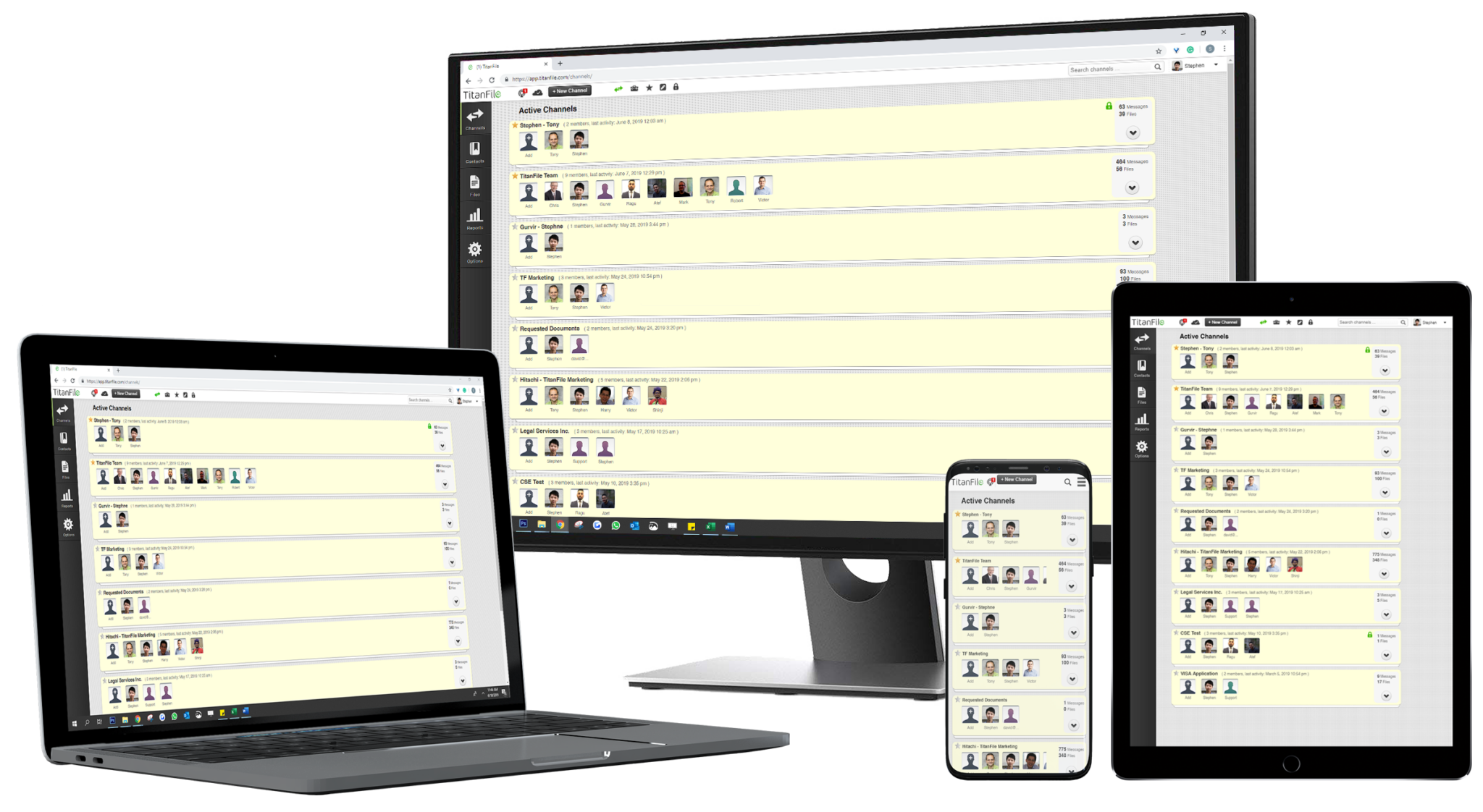
The Easiest and Most Secure Way to Share Files
Ranked #1 in Security
Consistently rated as the #1 most secure file-sharing platform on the market. Combined with state-of-the-art security capabilities and compliance certifications such as:
✔️ Encryption in transit and at rest
✔️ ISO 27001, SOC 2 Type II, PIPEDA, and HIPAA Compliant
✔️ Data residency in the US, Canada, or Europe

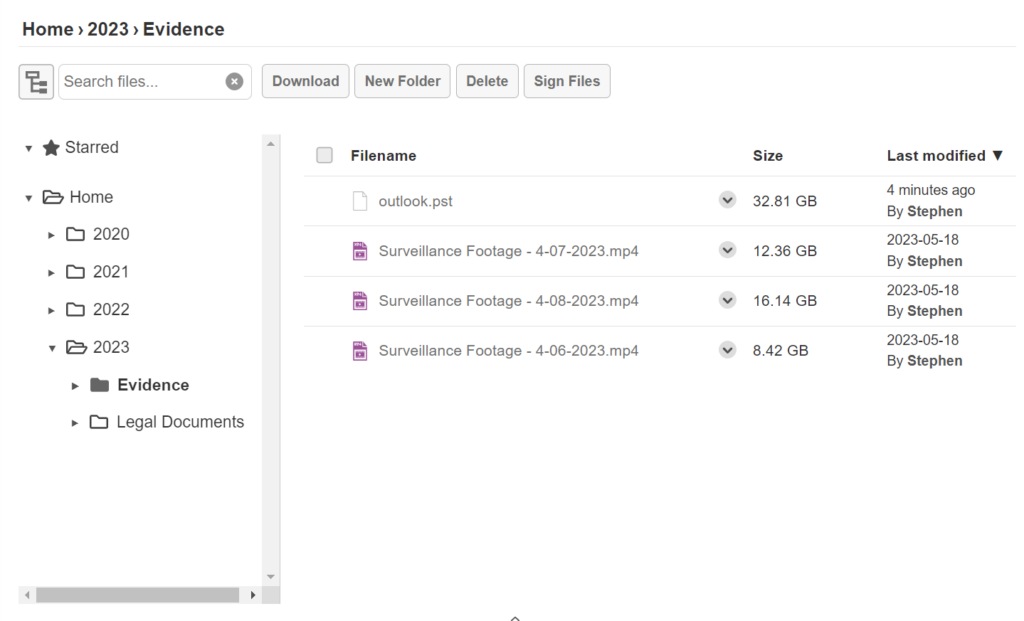
Large File Transfer
The most robust file transfer capabilities on the market. Upload files that are 100GB+ with ease.
✔️ No limits on file sizes or quantity
✔️ As much storage as you need
✔️ Upload folder structures without zipping
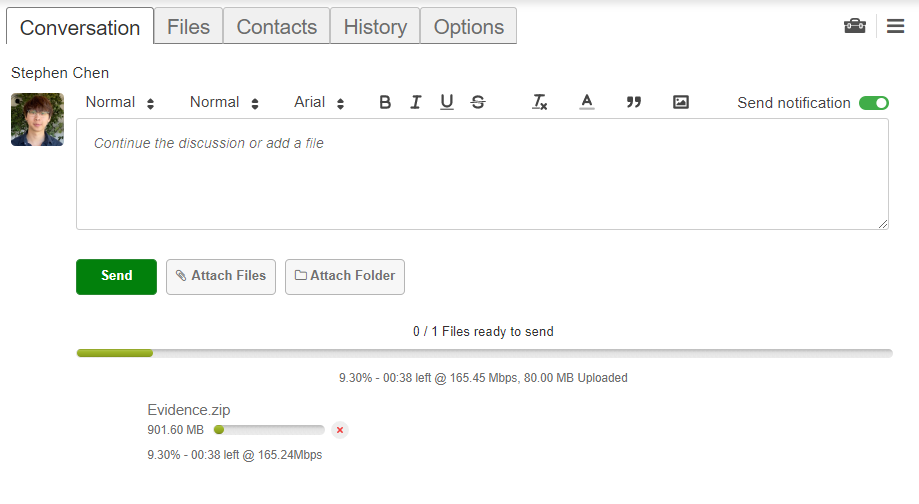
Lightning-Fast Performance
Unlock the fastest upload speeds on the market. Transfer files at lightning-fast upload speeds of up to 150Mbps.
✔️ Send gigabytes of data within minutes
✔️ Improve efficiency with quicker turnaround times
✔️ Super snappy and slick user experience
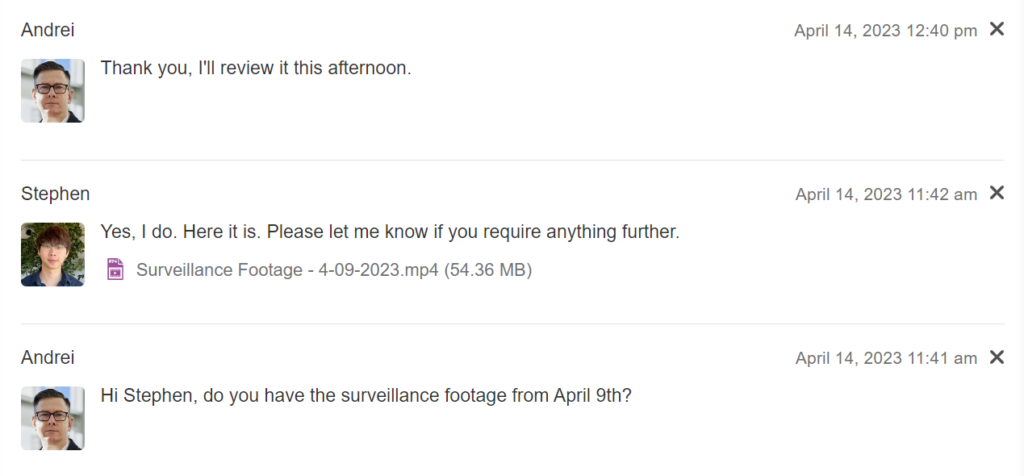
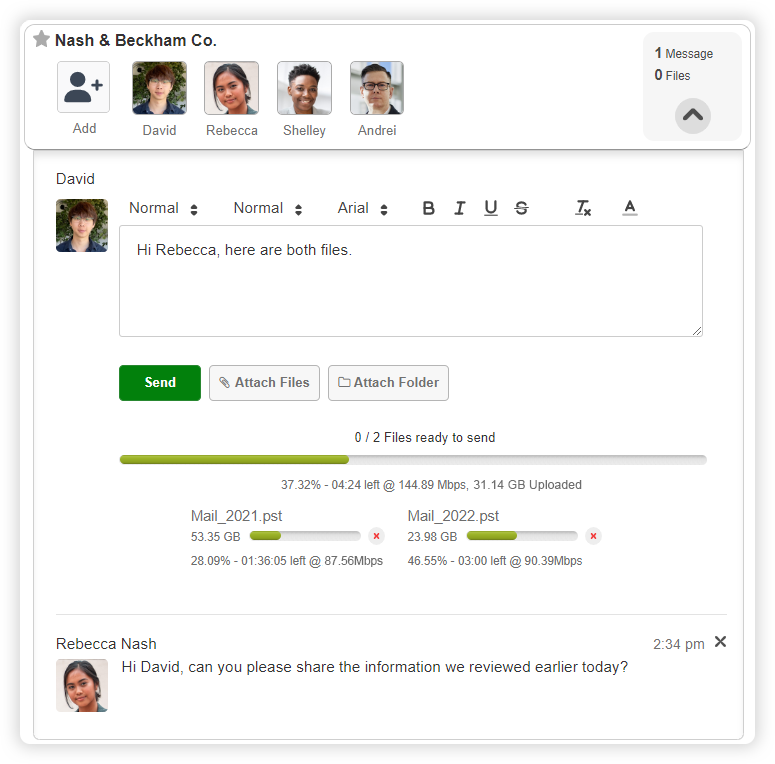
As Easy to Use as Email
Create secure workspaces to collaborate with your clients or other external contacts. In these workspaces, you can send and receive an unlimited number of files and messages.
✔️ Easy platform adoption
✔️ No help from IT is required
✔️ User-friendly interface
Testimonials From Valued Clients
“ The TitanFile team was excellent in ensuring that we had a smooth transition onboarding 1200 employees. When we initially introduced the product to our employees, they found the platform easy to access, easy to use, and reliable. The positive feedback from our staff convinced us that TitanFile was the solution for us. ”
" We really gauge the success of a product by three main things: reliability, usage and feedback from users. TitanFile has passed all of these metrics with flying colors, and we have been very happy with the solution. "
" If you’re looking for a secure file sharing solution with self-serve capability and a focus towards increasing the agility of the business, TitanFile ticks those boxes. "
" The TitanFile team has been incredibly resourceful and perfectly responsive at all times. TitanFile is exactly what we needed to grow our business. The move to partner with you and your organization has been one of my better decisions. You know it was a good decision you made in your life or your business when it is hard to remember a time without. "
" TitanFile allows our firm to react efficiently and securely to demanding legal document distribution and exchange. Our clients and partners embrace the simplicity of this powerful, protected solution. "
" To us at Dietrich Law, with gigabytes of information to transmit every day, TitanFile is the best, most reliable and safest solution where internet security, privacy and information costs are concerned. TitanFile is easy to use and is always reliable. "
" Simple, secure and stress free file transfer at its best. "