Cybersecurity & Data Privacy Blog
Resources to help keep your workplace up to date with cybersecurity and data privacy best practices.
Platform Update: New Features20130507080642
Platform Update: New Features
May 7, 2013
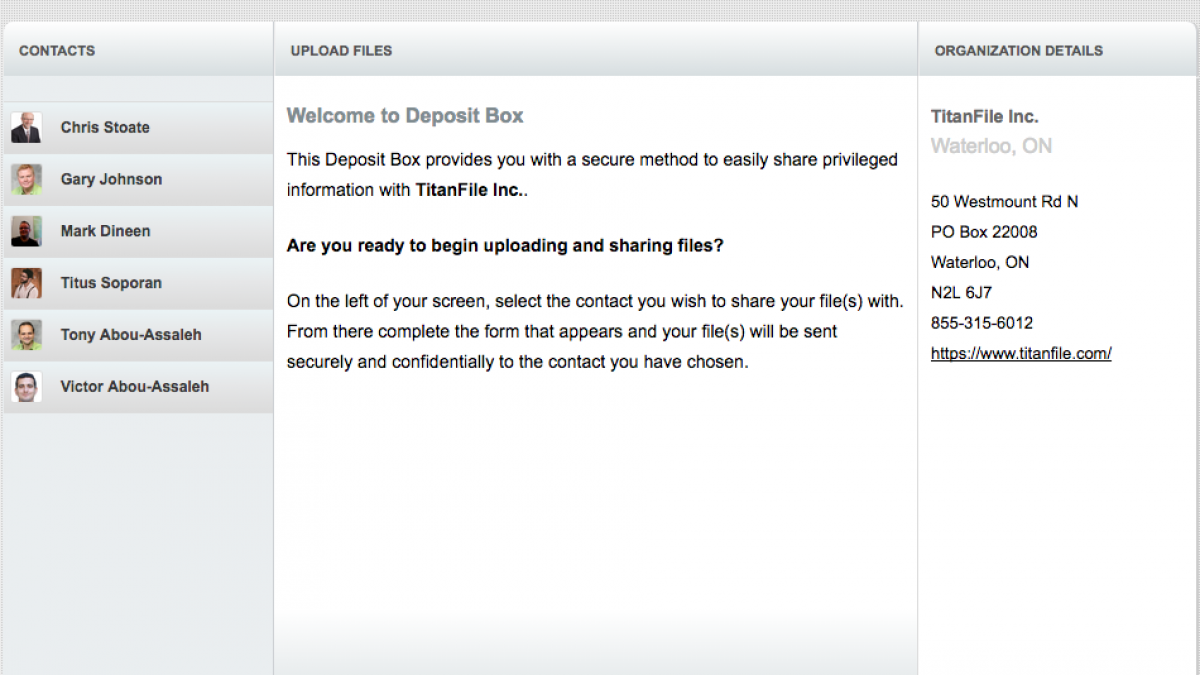
Introducing the TitanFile Secure Deposit Box20130506173135
Introducing the TitanFile Secure Deposit Box
May 6, 2013
Planning for a Worst-case Scenario20130506134730
Planning for a Worst-case Scenario
May 6, 2013
How do you Define Online Privacy?20130502152543
How do you Define Online Privacy?
May 2, 2013
Cybersecurity: A Global Issue20130501125055
Cybersecurity: A Global Issue
May 1, 2013
How to Protect your Mobile Device20130430140640
How to Protect your Mobile Device
April 30, 2013
4 Benefits of Developing a Corporate Culture Focused on Collaboration20130429123727
How to Create a Corporate Culture Focused on Security20130423151714
How to Create a Corporate Culture Focused on Security
April 23, 2013
5 Key Characteristics of Successful Telecommuters20130422142046
5 Key Characteristics of Successful Telecommuters
April 22, 2013
The Next Generation of Secure Passwords20130412151907
The Next Generation of Secure Passwords
April 12, 2013
How to Prevent Internal Data Leaks20130411120744
How to Prevent Internal Data Leaks
April 11, 2013
Three Reasons to Let SaaS do Your Heavy Lifting20130410105926
Three Reasons to Let SaaS do Your Heavy Lifting
April 10, 2013