How to Create a Strong Password20221108134753
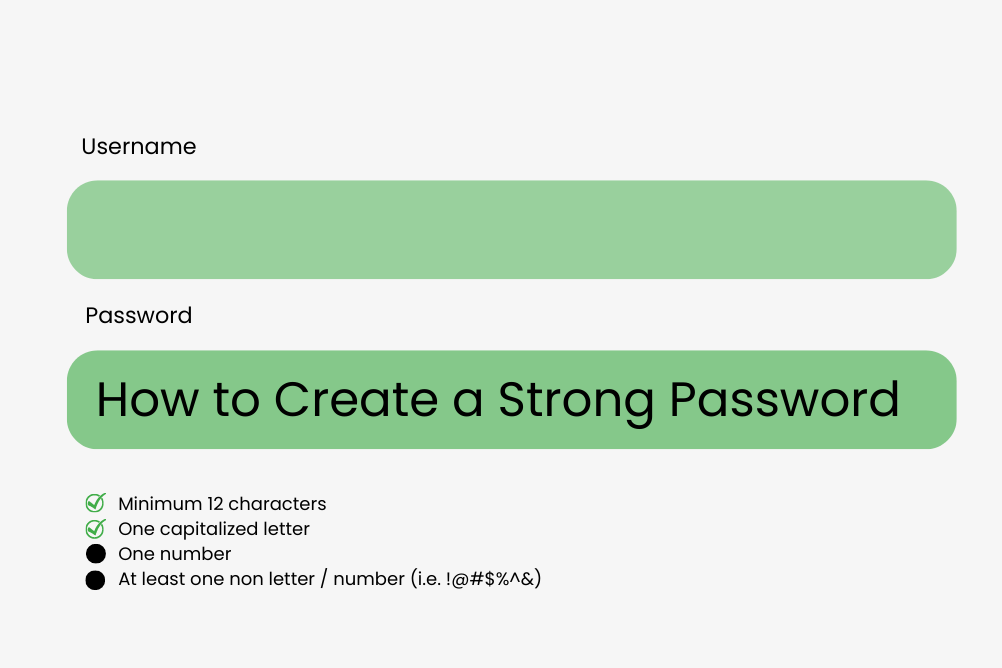
How to Create a Strong Password
Mark DineenNovember 8, 2022**, email security, information security, password security, security breach0 comments
Introduction One of the most common topics in relation to security is passwords. Virtually every account on the internet – from social media to ...
Why Collaboration is Important for Your Business20130318102426
Why Collaboration is Important for Your Business
Tony Abou-AssalehMarch 18, 2013**, collaboration, corporate knowledge, online collaboration, organizational knowledge, teamwork0 comments
Many hands make light work. Teamwork divides the task and multiplies the success. In business, there’s a lot of talk about the power of the collective...
Protecting Your Company After an Employee Leaves20130315131127
Protecting Your Company After an Employee Leaves
Tony Abou-AssalehMarch 15, 2013**, hack, hacker, internal breach, internal security, IT department, Matthew Keys, password security, two factor authentication0 comments
When an employee leaves a company, especially on bad terms, there’s always a risk that they could try to negatively impact your organization in ...
How Private are Work Email Accounts?20130311121525
How Private are Work Email Accounts?
Tony Abou-AssalehMarch 11, 2013**, corporate email, data leak, email privacy, hack, Harvard University0 comments
Harvard University has recently come under fire for hacking into the email accounts of 16 resident deans last fall in an attempt to determine who was ...
Is HIPAA Protecting your Privacy?20130301082312
Is HIPAA Protecting your Privacy?
Mark DineenMarch 1, 2013**, data breaches, healthcare, HIPAA, HITECH, privacy, security, security leaks0 comments
Signed by President Bill Clinton, the Health Insurance Portability and Accountability Act [HIPAA] of 1996 was enacted to protect the privacy rights of...
What if your Security is Breached? 3 Lessons Learned20130228123319
What if your Security is Breached? 3 Lessons Learned
Tony Abou-AssalehFebruary 28, 2013**, data leak, external penetration testing, HRSDC, Human Resources and Skills Development Canada, security breach, sony, wyndham hotels, zappos0 comments
You had backups to your backups, plans in place, and security that you had faith in. But it still happened. Your systems were breached and customer da...
How to be Successful at Working Remotely20130222102215
How to be Successful at Working Remotely
Tony Abou-AssalehFebruary 22, 2013**, collaboration, google hangout, skype, working remotely0 comments
Working remotely can be a winning experience. People speak of how they now have more time with their families, less of their life wasted on commuting,...
How to use Security and Privacy as a Competitive Advantage20130221193442
How to use Security and Privacy as a Competitive Advantage
Tony Abou-AssalehFebruary 21, 2013**, business, competition, data breaches, privacy policy, security policy, trust0 comments
Create a selling feature that puts you ahead of your rivals. That’s business 101, right? But sometimes it can be difficult to decide exactly wha...
5 Things to Consider When Choosing a Secure File Sharing Provider20130220123828
5 Things to Consider When Choosing a Secure File Sharing Provider
Tony Abou-AssalehFebruary 20, 2013**, audit trail, collaboration, data breaches, encryption, mobile device, secure file sharing, security0 comments
Has your office been thinking about secure file sharing lately? Whether it’s because of the constant stream of news stories on data breaches, or...