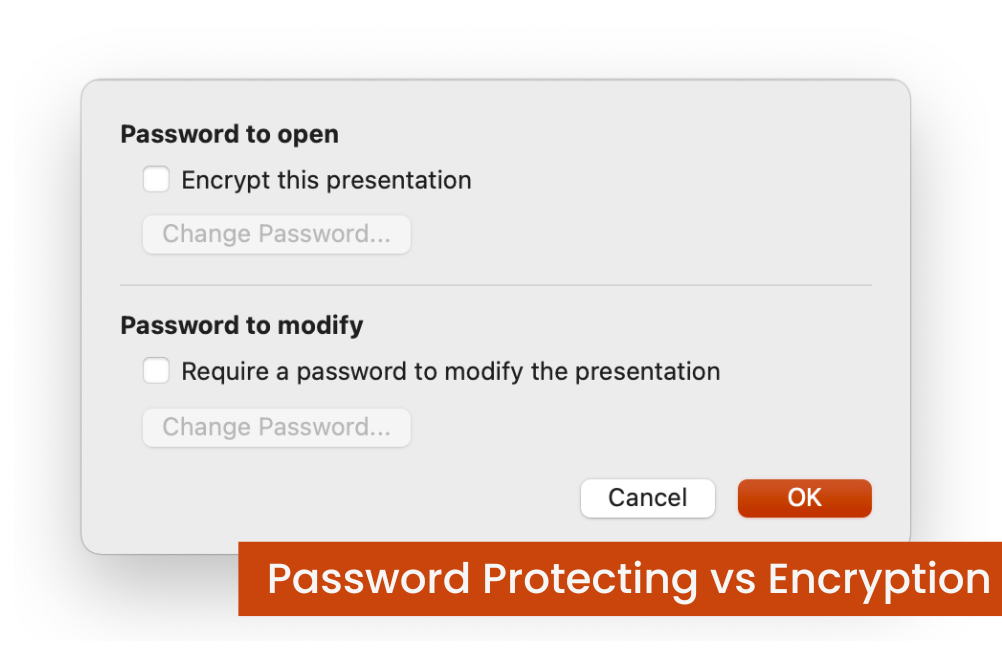
Password Protection vs Encryption: Why Encryption is More Secure20240413152206
Password Protection vs Encryption: Why Encryption is More Secure
When it comes to the security of confidential information, the internet can be a very non-secure place. However, there are various methods to protect ...
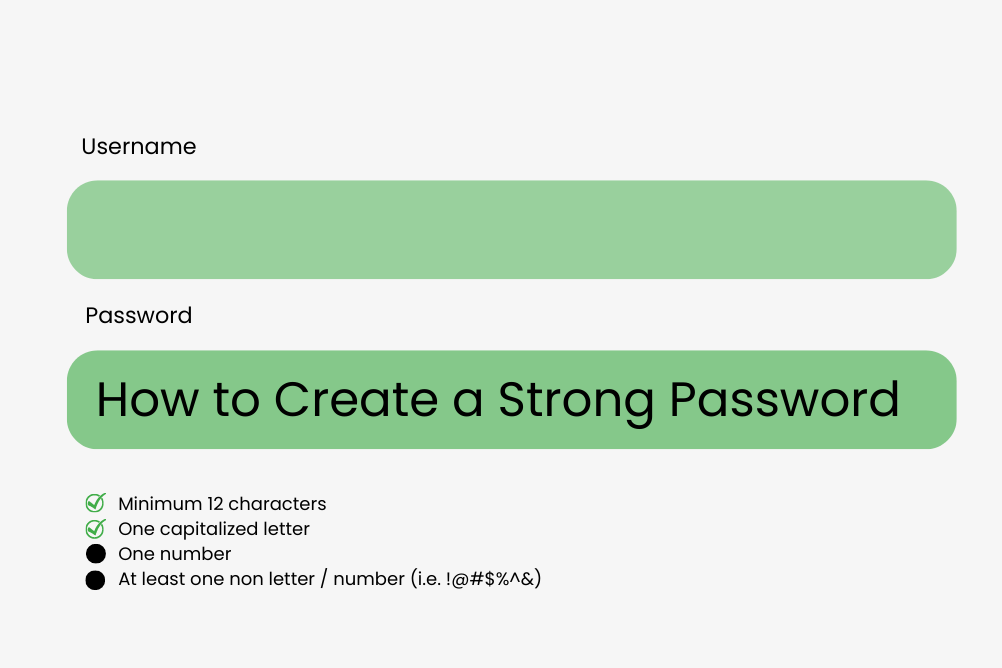
How to Create a Strong Password20221108134753
How to Create a Strong Password
Mark DineenNovember 8, 2022**, email security, information security, password security, security breach0 comments
Introduction One of the most common topics in relation to security is passwords. Virtually every account on the internet – from social media to ...
Could we Live in a Password-free World?20130513153526
Could we Live in a Password-free World?
We’ve all been there. Answering security questions, clicking ‘forgot my password’ and just generally wishing for a better way to pro...
Protecting Your Company After an Employee Leaves20130315131127
Protecting Your Company After an Employee Leaves
Tony Abou-AssalehMarch 15, 2013**, hack, hacker, internal breach, internal security, IT department, Matthew Keys, password security, two factor authentication0 comments
When an employee leaves a company, especially on bad terms, there’s always a risk that they could try to negatively impact your organization in ...
Building a Relationship with your IT Department20130212100341
Building a Relationship with your IT Department
Tony Abou-AssalehFebruary 12, 2013**, Cloud security, IT department, password management, password security, secure file sharing0 comments
Working in an IT department can sometimes seem like a thankless job. Think of the last time you reached out to your IT professional. You were probably...
5 Ways to Protect Yourself Online20130208141224
5 Ways to Protect Yourself Online
With data breeches being reported at an alarming rate, it’s important to take stock of how you protect your identity online. In your offline life you&...