In asymmetric public key cryptography, you have a key pair: one key is public (shared openly), and the other is private (kept secret).
These keys are mathematically linked inverses; data encrypted with the public key can only be decrypted with the corresponding private key, and vice versa.
In this guide, we’ll break down the difference between public key vs private key and their use in a cryptographic key pair.
Public Key vs Private Key: A Side-by-Side Comparison
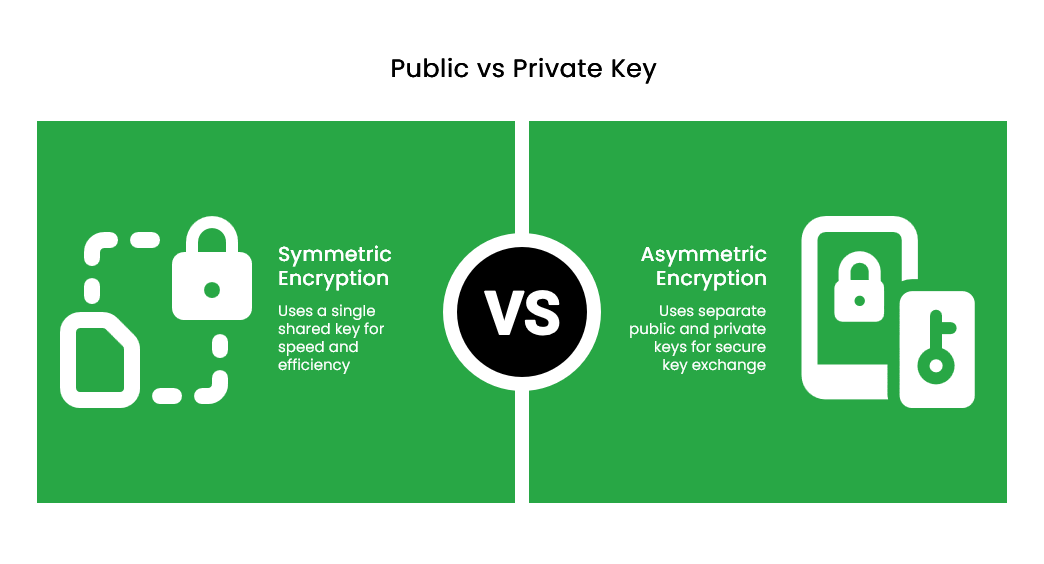
While public and private keys are used to protect data, they function very differently in how they encrypt and are shared, scaled, and secured. Here’s a side-by-side comparison:
| Aspect | Public Key (Asymmetric Encryption) | Private Key (Symmetric Encryption) |
| Number of Keys | Uses two keys: one public, one private. | Uses one key shared between sender and receiver. |
| Sharing | Public key can be shared openly. The system stays secure as long as the private key is kept secret. | Key must be shared privately. If it leaks, the entire communication is compromised. |
| Use in Encryption | Anyone can encrypt with the public key, but only the private key holder can decrypt. | Both sender and receiver use the same key for both encryption and decryption. |
| Speed and Complexity | Slower and more resource-heavy due to complex math (e.g., RSA encryption). | Much faster and uses shorter keys for similar security levels. |
| Scalability | Scales well — share your public key with anyone, and they can send you encrypted data securely. | Doesn’t scale well. You’d need a unique shared key for every connection, which gets messy fast. |
| Functions Enabled | Enables digital signatures, end-to-end encryption, and secure identity verification. | Provides confidentiality and integrity, but can’t verify sender identity or prevent denial (non-repudiation). |
What Is Public Key Encryption and How Does It Work?
Public key encryption (asymmetric encryption) is a way to protect data using two separate keys: a public key and a private key. The public key is shared with anyone, and the owner keeps the private key secret.
When someone wants to send you a secure message, they use your public key to encrypt it. Only your private key can unlock it. This keeps the data private, even if it travels through public networks.
A Reddit user explains it by analogy: “Your private key is the key, your public key is the lock.” You can give the lock (public key) to anyone. They can snap it onto a box (encrypt a message to you) and send it back, but only your private key can open that lock to get the content out.
This system is used in TLS encryption, email encryption, digital wallets, and other secure communication forms.
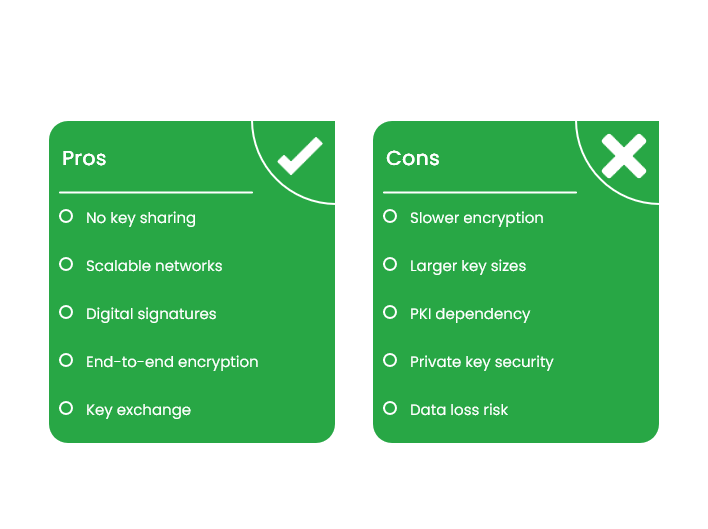
Advantages of Public Key Encryption
- No need to share a secret key ahead of time
- Scales well across large networks
- Enables digital signatures for identity verification
- Makes end-to-end encryption possible
- Helps exchange keys for faster symmetric encryption
- The public key can be openly shared without security risks
- Works well for one-to-many secure communication
Limitations of Public Key Encryption
- Slower than symmetric encryption
- Uses larger key sizes for similar security
- Needs trusted methods to verify public keys (PKI)
- Private key must stay absolutely secure
- If the private key is lost, data is unrecoverable
- Doesn’t always support forward secrecy
- Vulnerable to future quantum attacks
- Complex to implement and manage correctly
- Can be too heavy for small devices or high-speed needs
What Is Private Key Encryption and How Does It Work?
Private key encryption (symmetric encryption) uses a single shared secret key to encrypt and decrypt data. Unlike public key encryption, where the keys are different, symmetric encryption means both the sender and receiver must have the same exact key and keep it hidden.
The sender encrypts the message using the secret key. The receiver, who already has that key, uses it to decrypt the message. If someone else intercepts the message without the key, they’re out of luck (all they’ll see is scrambled data).
Symmetric encryption is especially useful after the first handshake (which might use asymmetric encryption) to exchange the secret key. After that, symmetric methods take over to protect the data with speed and minimal load.
Common symmetric algorithms include AES, ChaCha20, and older ones like DES.
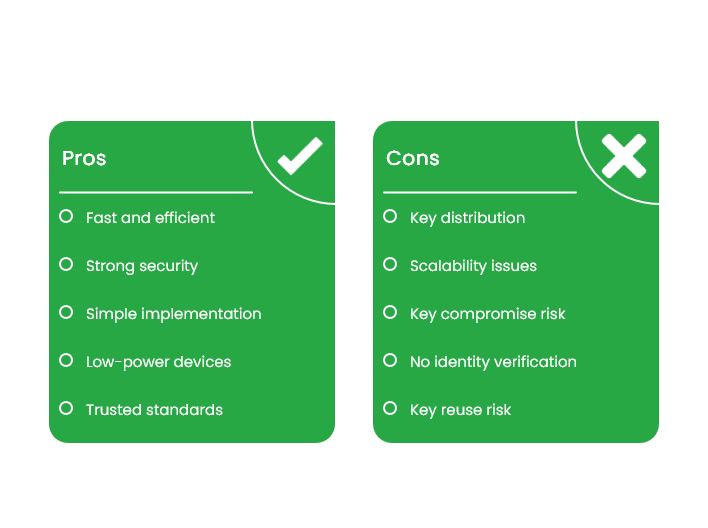
Advantages of Private Key Encryption
- Very fast and efficient for large data
- Strong security with proper key lengths (e.g. AES-256)
- Simpler to implement and manage in small environments
- Works well on low-power devices
- Trusted, widely used standards (like AES)
- Ideal for data at rest and ongoing secure communication
- Supports key rotation and session-level secrecy
- Can use HMACs for message integrity and authentication
Limitations of Private Key Encryption
- Both parties need the same key before communication
- Sharing that key securely can be tricky
- Doesn’t scale well to large groups (too many keys to manage)
- Anyone with the key can decrypt or forge messages
- No way to verify identity (no digital signature support)
- Reusing keys or poor key storage can lead to breaches
- Cannot start secure communication unless the key is already known
How Public and Private Keys Work Together
Private-public key encryption is often used in tandem, complementing each other’s strengths. The typical pattern is to use public key cryptography to establish a secure channel or share a secret key and then switch to symmetric encryption actually to transmit data.
Using public and private keys together, systems achieve:
- Confidentiality: via the symmetric cipher for content.
- Secure key agreement: via the asymmetric exchange.
- Authentication: via certificates or digital signatures (asymmetric).
- Integrity: via MACs or signatures.
None of these goals could be met as efficiently by either method alone.
TitanFile is a secure client collaboration platform that enables professionals to exchange confidential files easily. It uses a hybrid encryption approach, encrypting file contents with AES-256 (symmetric encryption) for speed and then securing the file’s access key with each recipient’s public key (asymmetric encryption) to ensure only authorized access.
Real-World Example: How TLS/SSL Uses Public and Private Keys
TLS (or SSL) keeps your web traffic safe (see that little padlock icon in your browser). Here’s how it uses both public and private keys together:
The server has a public-private key pair. It sends the public key to your browser in a verified certificate. Your browser checks that the certificate is valid and that it belongs to the website you’re visiting.
Next, both sides agree on a shared secret key by encrypting it with the server’s public key (RSA) or using a secure math trick like Diffie-Hellman. This part relies on asymmetric encryption.
Once they have the shared secret, they switch to symmetric encryption (like AES or ChaCha20) to encrypt your data because it’s much faster.
Which Encryption Key Type Is Best for Your Business?
The real answer isn’t “public key vs private key.” It’s how to use both to build a secure, scalable, and efficient system. Almost every modern security solution combines asymmetric encryption for key exchange and identity with symmetric encryption for speed and data protection.
Here’s when to use each:
Use asymmetric (public/private key) encryption when:
- You need to share encrypted data with someone for the first time without a shared secret
- You want to verify identities or digitally sign confidential documents, software, or emails
- You’re building or using end-to-end encrypted systems where only recipients can decrypt
- You need scalable encryption for multiple clients, partners, or users
Use symmetric (private key) encryption when:
- You’re encrypting large files, databases, or backups that require high performance
- You need to meet compliance requirements for encrypting data at rest
- You’re securing digital communication across a known, internal system (like a VPN)
- You’re working with older or low-power devices that can’t handle public key operations
In most cases, you’ll use both together. For example, secure file-sharing platforms, like TitanFile, encrypt the file using symmetric encryption and then encrypt the file’s key with each recipient’s public key. That’s how end-to-end encryption and data confidentiality are handled in practice.
TitanFile enables accounting firms like Crowe Soberman to securely collect and organize sensitive documents from clients year-round—all protected by strong encryption and Canadian data residency.
Threats to Public and Private Key Encryption
Here are the top threats to both public and private key encryption:
- Key Compromise (The Human Element): If attackers steal private or symmetric keys through phishing, malware, or poor storage, they can decrypt data or impersonate users. This is one of the most common real-world failures.
- Brute Force and Weak Algorithms: Outdated encryption like DES or RSA-512 can be cracked with enough computing power, especially as hardware gets faster.
- Quantum Computing Threat: Future quantum computers could break RSA and ECC encryption using Shor’s algorithm, compromising public key systems.
- Man-in-the-Middle (MITM) Attacks: If someone tricks you into trusting a fake public key or certificate, they can intercept encrypted data undetected.
- Weak Random Number Generators: Poor or predictable randomness can lead to weak or reused keys, making systems easy to break.
- Obsolete Protocols and Crypto: Legacy algorithms like SSLv3, RC4, SHA-1, or 3DES have known vulnerabilities and are actively exploited.
- Brute Forcing Weak Passwords: If encryption keys are based on weak passwords, attackers can guess them using dictionary or brute force attacks.
- Physical Theft of Devices: If a device storing keys is stolen and the keys are accessible, encryption is useless.
Why Key Management Matters
To address these threats to your key encryption:
- Keep your cryptosystems updated (patches for libraries, only use strong protocols).
- Employ strong operational security around keys (limit access, use HSMs or key vaults, rotate keys, monitor usage).
- Educate users/administrators about the importance of not bypassing warnings (like TLS certificate warnings), which could expose them to MITM.
- Plan for the long term (e.g., have a strategy for post-quantum migration for data with long confidentiality requirements).
Real-World Examples of Encryption Implementation
Let’s look at real-world examples how symmetric and asymmetric encryption work together in practice:
Sending Sensitive Docs to Clients
You upload a contract for your legal client to TitanFile. The file is encrypted with a symmetric key (AES-256), which is then encrypted with your client’s public key. When your client logs in, their private key unlocks the file key.
TitanFile enables law firms like Littler to manage secure, large-scale data transfers using layered encryption, over 46 TB of data was encrypted and shared across 10,000+ workspaces in just one year.
“In the last year alone, we used TitanFile to securely transfer over 46 terabytes of data using over 10,000 workspaces.
With over 1800 lawyers practicing in 90 offices across 30 countries, we only select technology that offers best-in-class information security; and this is the key reason why we chose TitanFile as our secure transfer platform.”
– Paul Weiner, National eDiscovery Counsel
Messaging Apps
You message your client on WhatsApp. Your app gets your client’s public key, encrypts a session key, and sends it. That key is then used to encrypt all your chats. Even WhatsApp can’t read them. Only your client’s phone can decrypt using their private key.
Banking
You swipe your card at an ATM. The ATM’s hardware encrypts your PIN using Triple DES, and it is then sent securely to the bank.
Meanwhile, the connection from your phone banking app is secured via TLS, using a mix of public and private key crypto.
Secure Your Client Files with TitanFile
Most breaches today don’t happen because encryption fails. They happen because the tools around it are weak or misused. TitanFile takes that risk off your plate. With end-to-end encryption, access control, and secure client portals, it ensures your confidential files stay protected and confidential.
TitanFile is compliant with industry-leading standards including SOC 2 Type II, ISO 27001, HIPAA, PIPEDA, and GDPR, with the option to store data in Canadian, U.S., or EU data centers.
Don’t leave encryption to chance. Use a secure file-sharing platform like TitanFile and stay compliant, professional, and protected. Try Titanfile secure file for free. It’s as easy to use as email.
Frequently Asked Questions
Which encryption key type Is more secure?
Both keys are secure when used correctly. Symmetric keys are faster and great for large data. Asymmetric keys (public/private) add identity verification and are better for sharing data securely. Most systems use both together for the best balance of security and speed.
What is a cryptographic key?
A cryptographic key is a string of bits used by an encryption algorithm to lock (encrypt) or unlock (decrypt) data.
How are public and private keys generated?
They’re created as a pair using mathematical algorithms like RSA or elliptic curve cryptography. The private key is random and secret. The public key is mathematically linked to it but can’t be used to figure out the private key.