In today’s digital landscape, the ability to understand “how to share files securely” has become increasingly important for businesses and individuals alike. As data breaches and hacking incidents continue to make headlines, it’s crucial to ensure that sensitive information remains protected while being shared.
This blog post will explore various methods and solutions for securely sharing files, emphasizing the significance of data protection, privacy, and compliance with regulations.
Key Takeaways
- Secure file sharing is essential for data security, privacy and compliance with regulations.
- Solutions such as cloud storage services, encrypted protocols and peer-to-peer networks offer secure file transfer.
- Adopting best practices such as encryption, strong passwords & two factor authentication can help ensure secure file sharing.
The Importance of Secure File Sharing
Safeguarding data security, maintaining privacy, and adhering to regulations are key reasons why it’s important to share files securely. Both business users and individuals should opt for a dependable secure file sharing service that offers strong encryption and control access features.
Failing to do so can lead to data breaches, loss of sensitive information, and potential legal ramifications.
Data Protection and Privacy
Businesses and individuals uphold trust and prevent unauthorized access to confidential information by prioritizing data protection and privacy when seeking secure file sharing methods. One of the most effective ways to ensure data protection and privacy is through encryption. File encryption software, which can be integrated into file sharing software, utilizes cryptographic algorithms to render data unreadable to unauthorized users without the correct key to decrypt or unlock it, thus providing a layer of security for data.
Utilizing consumer-grade file-sharing services in the workplace may result in:
- Intellectual Property loss
- Sensitive data leakage
- Loss of visibility and control over where data resides
- Potential compliance, regulatory, and e-discovery violations
Using a dedicated user account for secure file sharing in a business environment can mitigate these risks.
End-to-end encrypted cloud storage, such as zero-knowledge cloud storage, ensures the highest level of security, as the provider does not have access to the files’ encryption keys, providing the ability to share sensitive information without risking security or privacy.
Compliance with Regulations
Adhering to data protection regulations is imperative for businesses to avert penalties and legal ramifications. The consequences of failing to adhere to data protection regulations can be severe, as organizations may be subject to sanctions and fines.
Hence, choosing a secure file sharing solution that complies with regulations like the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) is pivotal.
Understanding Different File Sharing Methods
There are various methods for secure file sharing, including cloud-based services, encrypted file transfer protocols, and peer-to-peer networks. Understanding the differences between these methods, each offering its own advantages and security features, can help determine the solution that best fits your needs.
Cloud-Based Services
Cloud-based services provide a convenient and accessible approach to secure file sharing, with encryption and access controls in place. Services like iCloud Drive, OneDrive, and Wormhole offer various features, such as file sharing, synchronization, and version control, making it easy for users to store and share their files securely.
Cloud-based file sharing services offer several security features to protect your data:
- Encryption techniques like the Advanced Encryption Standard (AES) and file-based encryption are used to protect data from unauthorized access.
- Access control features allow you to control who can access your files and folders.
- Secure sharing options ensure that your sensitive information remains protected when sharing with others.
These security measures provide peace of mind and help keep your data safe in the cloud.
Following secure file sharing best practices, like encrypting files prior to sharing, using strong passwords and two-factor authentication, and limiting access while tracking activity is important.
Encrypted File Transfer Protocols
Encrypted file transfer protocols, such as Secure File Transfer Protocol (SFTP) and FTPS (FTP over SSL/TLS), provide secure methods for transferring files across networks. These protocols employ encryption to secure the data in transit, achieved through the utilization of a combination of public and private keys, which authenticate the sender and receiver of the data.
Utilizing encrypted file transfer protocols offers a secure means of transferring files across networks, ensuring that the data remains confidential and can only be accessed by the intended recipient. Moreover, they provide an extra layer of security as the data is encrypted and cannot be intercepted or tampered with by anyone other than the sender and receiver.
Peer-to-Peer Networks
Peer-to-peer (P2P) file transfer eliminates the necessity for a centralized server that stores the data. Individual clients link to a distributed network of peers. They complete the file transfers across their respective network connections..
While P2P file transfer options tend to be more expeditious than cloud-based services and do not necessitate a third-party provider, it is not advisable to use P2P file sharing for sharing sensitive files. To preserve user privacy when using P2P file sharing, it’s essential to utilize a Virtual Private Network (VPN) as an additional security measure.
Best Practices for Secure File Sharing
Following best practices such as pre-sharing file encryption, using robust passwords and two-factor authentication, and limiting access along with activity monitoring, are vital to maintain secure file sharing while sharing files.
Implementing these practices can significantly reduce the risk of data breaches and unauthorized access to sensitive information.
1. Encrypt Files Before Sharing
Encrypting files before sharing provides an additional layer of security, guaranteeing that only authorized recipients can access the data. By rendering the data unreadable to unauthorized users, encryption ensures that sensitive information remains protected during the file-sharing process.
2. Use Strong Passwords and Two-Factor Authentication
Employing strong passwords and two-factor authentication assists in safeguarding files from unauthorized access. Two-factor authentication (2FA) is a security measure that requires users to verify their identity by entering a six-digit code from an authenticator app or activating a physical security key for added protection.
Using strong passwords and 2FA can significantly enhance the security of your files and accounts.
3. Limit Access and Monitor Activity
Limiting access to shared files and monitoring activity can help prevent data breaches and unauthorized access. Access control is a security technique that regulates the viewing and utilization of resources within a computing environment.
By monitoring file access, you can track whether a file has been downloaded and revoke access if necessary, thwarting unauthorized access and detecting suspicious activity.
Top 7 Secure File Sharing Solutions
This blog post examined the top 7 secure file sharing solutions:
- TitanFile
- Tresorit
- Sync.com
- pCloud
- Proton Drive
- Resilio Sync
- Nextcloud
Each solution stands out with its unique features and security measures. Understanding their differences can help you pick the most suitable solution for your needs.
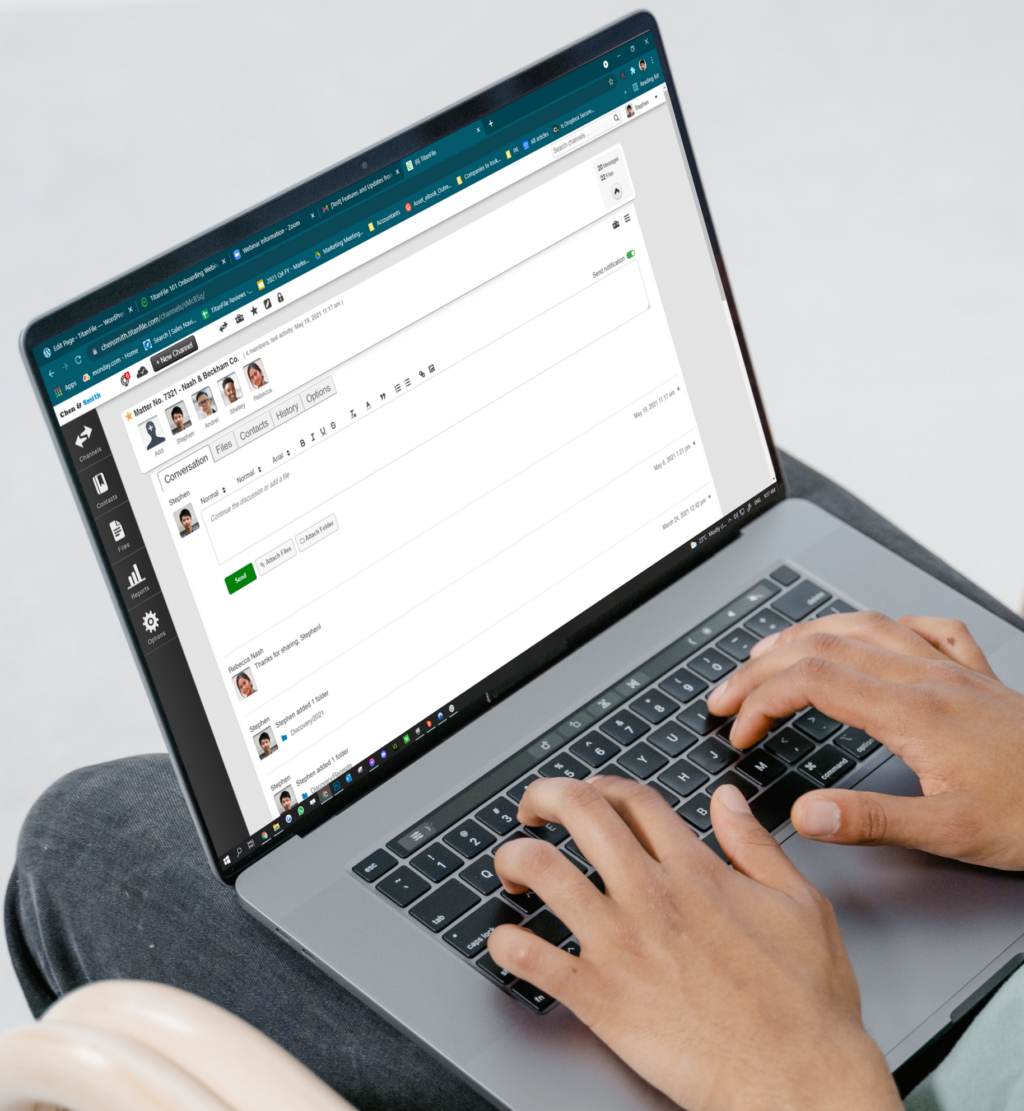
1. TitanFile

TitanFile is an award-winning secure file sharing and client collaboration platform, offering a secure method for professionals to communicate and share files with their clients. With encryption, access controls, and compliance features, TitanFile ensures that your sensitive data remains protected while being shared.
TitanFile is ISO 27001 certified and compliant with SOC 2 Type II, GDPR, HIPAA, and other regulations, providing audit logs and other features to ensure businesses meet their compliance requirements.
Get a 15-day free trial of TitanFile.
2. Tresorit
Tresorit is a cloud storage service that offers advanced encryption for file sharing and storage, providing end-to-end encryption to ensure the security of confidential information. With zero-knowledge encryption, Tresorit ensures that no one, not even Tresorit itself, can access the data stored on its servers.
Additionally, Tresorit provides a variety of privacy features, including the capacity to set expiration dates for shared files, password protection for shared files, and the capability to revoke access to shared files. Tresorit also adheres to a variety of regulations, including GDPR, HIPAA, and SOX.
3. Sync.com
Sync.com is a secure file storage and sharing platform that provides users with ease of use, speed, and security at an affordable price. It allows users to connect and sync their files across multiple devices and can also be utilized for backup purposes.
Sync.com offers comprehensive security features such as end-to-end encryption, zero-knowledge privacy, secure file sharing, and cloud storage. Additionally, it provides several additional features including version control, file locking, and access control.
4. pCloud
pCloud is a secure, encrypted cloud storage service that provides users with the ability to store and share their personal files. With encryption and access controls, pCloud ensures that your sensitive data remains protected while being shared.
pCloud employs 256-bit AES encryption and two-factor authentication to ensure the utmost security of your data. Compatible with Windows, Mac, iOS, and Android platforms, pCloud offers a versatile solution for secure file storage and sharing.
5. Proton Drive
Proton Drive is a secure and encrypted cloud storage service created by Proton, providing users with complete control over their data. With Proton Drive, you can:
- Store your files securely in the cloud
- Enjoy end-to-end and zero-access encryption for maximum privacy
- Share files with others while ensuring their security
- Access your files from any device, anywhere
Proton Drive is the perfect solution for those who prioritize data security and privacy.
Proton Drive seamlessly integrates with Proton Mail, Calendar, and VPN, enabling users to securely access their data across all Proton services.
6. Resilio Sync
Resilio Sync is a rapid and dependable file and folder synchronization solution for residential and corporate environments. Leveraging a peer-to-peer network, Resilio Sync securely transfers files between devices without the need for a central server.
With end-to-end encryption, secure file transfers, and two-factor authentication, Resilio Sync offers a secure solution for file sharing and synchronization.
7. Nextcloud
Nextcloud is a suite of client-server software providing file hosting services, enabling a modern, on-premises content collaboration platform with features such as real-time document editing, video chat, and groupware on mobile, desktop, and web. Offering encryption, access controls, and customization options, Nextcloud ensures secure file sharing and storage.
Additionally, Nextcloud provides features such as file versioning, file locking, and secure storage, ensuring that your sensitive data remains protected.
Addressing Common Security Concerns
Typical security risks associated with file sharing encompass data breaches and hacking. Following best practices and using secure file sharing solutions with robust encryption and access controls, as discussed in this blog post, can help mitigate these risks.
Encryption is a key component of secure file sharing solutions. It ensures that only authorized users
Data Breaches and Hacking
Data breaches are incidents wherein confidential, sensitive, or protected information is accessed without the authorization of the owner, resulting in its exposure to unauthorized individuals.
By using secure file sharing solutions with robust encryption and access controls, the risk of data breaches and hacking can be mitigated.
Trusting Third-Party Providers
One must evaluate the security measures, privacy policies, and compliance with data protection regulations of third-party providers when using them for secure file sharing. Assessing these aspects is necessary for establishing trust and ensuring that your sensitive information remains protected while being shared.
Summary
In conclusion, secure file sharing is essential in today’s digital landscape for protecting sensitive information and ensuring compliance with regulations. By understanding different file sharing methods, following best practices, and utilizing secure file sharing solutions such as TitanFile, Tresorit, Sync.com, pCloud, Proton Drive, Resilio Sync, and Nextcloud, businesses and individuals can securely share files without compromising data security or privacy.
Frequently Asked Questions
What is the most secure way to send documents?
The most secure way to send documents is by using encryption, which renders the file unreadable until it is decrypted.
What is the importance of encrypting files before sharing?
Encryption ensures that confidential data can only be accessed by the intended recipients, providing an extra layer of security when files are shared.
What are some examples of encrypted file transfer protocols?
Secure File Transfer Protocol (SFTP), FTPS (FTP over SSL/TLS), and SSH File Transfer Protocol (SFTP) are some examples of encrypted file transfer protocols that ensure secure and private data transfer.
How can I ensure that my cloud-based file sharing service is secure?
Ensure cloud-based file sharing security by using services that offer end-to-end encryption, access controls, and compliance with data protection regulations.

