Before diving into the world of two-factor authentication, it’s better to learn more about the basics first––the fundamentals, as they like to say.
With the rising amount of online accounts and web-based footprint comes the rise of more cyber criminals. Even if it’s just your email, your Facebook profile, or your deserted Twitter account, they will stop at nothing to claim it as their own. Whether you’re just a commoner or a big personality, hacks and data breaches will reach you one way or another.
Fortunately for you, business and individual accounts are entitled to add an extra layer of protection. This extra level is called ‘two-factor authentication’ or what’s referred to as 2FA in the online realm. There are plenty more practices that can protect your account, but 2FA stands tall on the email security list.
INSIDE THIS ARTICLE
What is Two-Factor Authentication?
As aforementioned, 2FA is an extended hand in security. Its goal is to confirm that the person who’s trying to get into the account is, expectedly, who they are.
Imagine logging into your email with your normal username and password. After that, it’s expected that you would already have access to your account––maybe even checking a couple of recent messages. However, if you have 2FA enabled, the platform will be asking more than just your username and password. Instead, you have to provide another piece of information to confirm who you are.
This piece of information could be asked in three different forms:
- Knowledge-based – Passwords, answers to security questions, or even your Personal Identification Number (PIN).
- Possession-based – A credit card, smartphone or hardware token.
- Inherence-based – Fingerprints, iris scans, or even your voice.
The Importance of Two-factor Authentication
In the past few years, there have been a couple of platforms that have reported data breaches and lost their users’ personal data. Given that technology has progressed further than before, cybercrime has also evolved to become even more polished. If a company decides to give in to traditional practices, it would be more vulnerable to attacks and external threats. As has been said, cybercriminals know no boundaries. Whether you’re a global company with multi-million stakes or a start-up venture, leaving a gap in your security will undoubtedly cause both financial and reputational loss––the beginning of the end, per se.
With no questions asked, what comes after a data breach is an unimaginable defeat. You see, these breaches are but catalysts for identity theft and so much more crimes. For one, stolen credentials result in fake credit cards and worse, shopping sprees. These shopping sprees aren’t your normal visits to Topman or American Eagle––there are hundreds of thousands lost in your account. In fact, these data breaches are basically 65% identity theft and because of that, more than $56 billion were lost in 2020
Numbers speak, don’t they? But this is the type of security online platforms have nowadays. In any case, these platforms should offer the tightest, if not tighter, security to their consumers. However, platforms are not the only ones that should move. Consumers, on the other hand, should also be aware of protecting their information––and just one single password isn’t going to cut it. You need one more layer, perhaps something stronger, and most consider that to be two-factor authentication or 2FA security.
The Benefits of Two-factor Authentication
Passwords are the necessary primary line of defense for keeping your personal accounts safe, but strong passcodes are difficult to keep track of. Too many people fall into the trap of using ones that are easily remembered. It might come as no surprise that the most used password in 2020 ranked by NordPass is ‘123456’. Accounts using that password have already been breached over 23 million times.
2FA is one of the most dependable security measures that can cater to everyone. If you have 2FA by your side, not even your password is enough to breach your account. Even if someone guessed your impossible password, it’s unlikely that they’ll have access to the secret code that was sent to your phone or know the name of your neighbor’s dog. If more platforms enforced security measures like this, they’d be worrying more about improving their systems instead of data breaches.
There are a few other benefits to TFA as well. Professionals will be happy to know that it fills compliance requirements for PCI, HIPAA, and PIPEDA if you ever need to transfer any protected health information. Additionally, two-factor authentication makes remote working a little safer – for those days you can’t make it in to work.
Types of Two-Factor Authentication
Eventually, you’ll realize that your only form of protection is your password. By then, hopefully, you would’ve understood that there’s a great chance of being hacked. This realization may lead you to either strengthen your password to a point of no return or just getting or enabling yourself the two-factor authentication system. If you’ve chosen the latter, then accept that you will be offered pristine security for your account and eliminate the chances of being hacked.
Though this may be true, that doesn’t mean that all two-factor authentication is the same in strength value. Currently, there are multiple platforms that utilize multiple types of 2FA and their strength varies from one another, but rest assured that it’s definitely better than your lonely passwords. Here are all the types of 2FA!
Hardware Tokens

Though this did offer some form of security, it just wasn’t feasible for businesses to distribute it left, right, and center. These units are costly, and distributing them is even costlier. The danger of losing it or getting it stolen are real possibility as well.
SMS or Message-based and Call-based 2FA
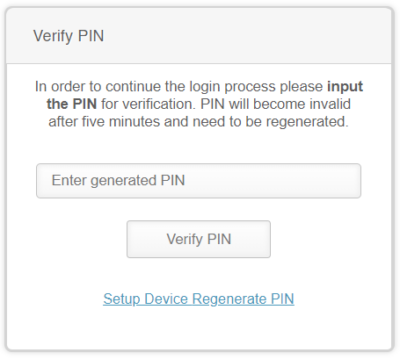
Many have described SMS-based 2FA to not be enough protection, though. Hackers are able to spoof a phone number and intercept a 2FA code. Still better than not having 2FA at all.
Software Token / Authenticator Apps

This form of two-factor authentication is, quite possibly, what tops the podium. It’s like a combination of the last two 2FA types wherein a software-generated and time-based OTP is given to the user.
In a way, it’s like the hardware token where the code only lasts for less than a minute. Combined with the convenience of SMS-based 2FA where it just goes directly to your phone, it’s 2FA innovation at its finest.
The way it functions is particularly different. The user must first download and install a free 2FA app––like Authy, Google Authenticator, or Vonage––on their phone and/or computer. This app works for any platform that supports two-factor authentications. After signing in, the app shows a code that serves as your OTP. What makes it better than SMS-based 2FA is since the code is both generated and displayed on the same device and app, it’s less prone to being hacked.
Since this app-based 2FA solution is available just about anywhere from your phones, laptops, desktops, and other gadgets, and even offline, this makes for one of the best two-factor authentications to exist in the current time.
Push Notifications
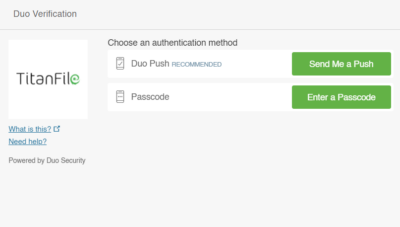
As a 2FA method, push notifications function very differently than the other 2FA methods we’ve described. Users can use apps like Duo to allow or deny access with just a single touch––no codes, no passwords, and takes no more than 5 seconds.
Inherently, this is a relationship between the app and the user. This eliminates threats of being hacked or having cybercriminals in the middle of your business. Push notifications as 2FA security is very much effective––user-friendly, too.
Biometrics

What is TitanFile?
TitanFile is an easy-to-use file sharing solution that allows you to securely exchange confidential documents and files with your clients and colleagues with peace of mind.

