Encryption is locking your data so no one else can read it. But there are real cases where one layer of encryption isn’t enough. Hackers can break in, and systems get compromised. That’s where double encryption comes in.
In this article, I’ll break down:
- What is double encryption?
- When it’s worth using (and when it’s probably not)
We will also discuss how security-conscious organizations, including law firms and healthcare providers, now rely on double encryption to safeguard their most sensitive data.
Here’s what you need to know:
What Is Double Encryption?
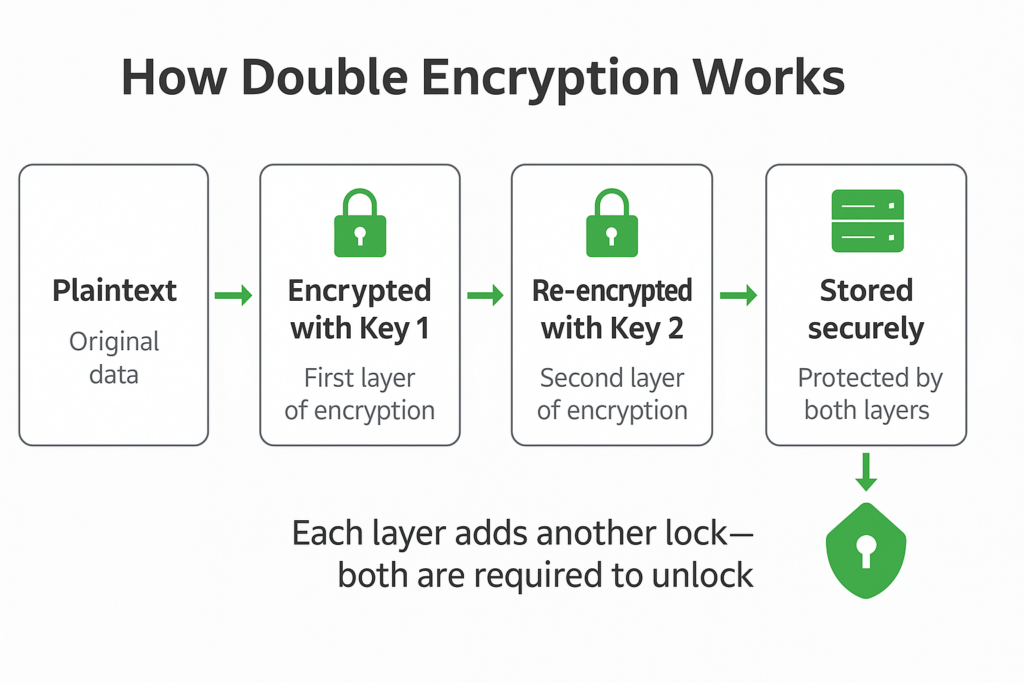
Double encryption means locking your data twice. Your data is encrypted once, and then the encrypted version is taken and encrypted again.
One encryption layer might not be enough. If the first key is exposed or the first algorithm has a vulnerability, your data is still locked by the second layer. That second layer can be the difference between a contained incident and a full-on data breach.
It works like this:
- You encrypt the data once using a secure algorithm and a key (Key 1)
- Then you encrypt that encrypted data again using a different key (Key 2) and possibly a different algorithm altogether
Titanfile is an encrypted file-sharing platform that uses encryption at rest and in transit and supports Customer-Managed Encryption Keys (CMEK) for clients needing total control. This means you get end-to-end security, even in untrusted cloud environments.
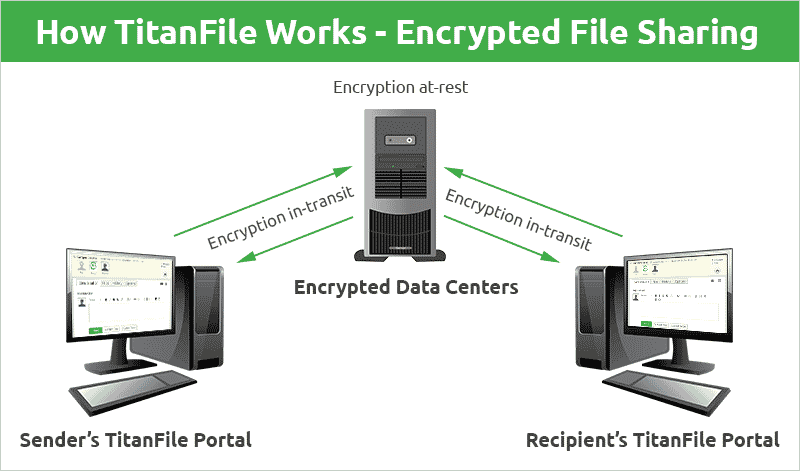
How Does the Double Encryption Process Work?
Here’s how multi-layer data protection plays out:
- First Layer: The system encrypts raw data (like customer records or financial info) using Key 1, creating encrypted output (ciphertext).
- Second Layer: That ciphertext is then encrypted again using Key 2. You might use a different algorithm for this second pass, adding diversity to your protection.
- Decryption Process: The data is decrypted in reverse. Key 2 removes the outer layer. Then, Key 1 decrypts the original content. Without both keys, access is impossible.
If one layer of protection fails, maybe due to a stolen key, a software bug, or a cracked algorithm, the second layer still protects your data. It removes that single point of failure.
| Aspect | Single Encryption | Double Encryption |
| Number of Encryption Keys | Uses one key (or key pair) for encryption and decryption. | Uses two independent keys—one per layer. |
| Layers of Encryption | One encryption layer is applied directly to the data. | Two layers are applied in sequence; the first output is re-encrypted. |
| Security Strength | Strong with modern ciphers and proper key management. | Stronger—adds a second barrier. If one fails, the other still protects data. |
| Impact of Key/Algorithm Compromise | If the key or algorithm fails, the data is exposed. | If one fails, the second may still keep data safe. No single point of failure. |
| Performance Overhead | Fast—just one encryption/decryption step. | Slower—requires two passes, increasing CPU load and latency. |
| Complexity & Integration | Easy to implement and manage. Fewer moving parts. | More complex setup and maintenance. Needs careful integration. |
| Key Management | One key to manage. Simple rotation and storage. | Two keys to managing securely. Increases the risk of key loss or mismanagement. |
| Use Cases | Ideal for most everyday applications like HTTPS, disk encryption, and emails. | Best for high-security needs—finance, healthcare, defence, or zero-trust cloud setups. |
To see how this works against brute force attacks, here are two examples that show when companies use single vs. double encryption:
Single Encryption Example:
Most websites today use HTTPS, which encrypts data using the TLS protocol. When a customer logs into their online banking portal, their username and password are protected by a single layer of encryption during transit.
Double Encryption Example:
Under its Commercial Solutions for Classified (CSfC) program, the U.S. National Security Agency (NSA) follows the “Rule of Two.” This principle requires that classified data be protected by two independent layers of encryption, each using separate cryptographic implementations, often from different vendors.
Types of Double Encryption
Here are the main types of double encryption that companies use:
- Symmetric-Key Double Encryption: Encrypt data twice using symmetric algorithms like AES, each with a different key. This method is often used in high-security environments.
- Hybrid (Asymmetric + Symmetric): Encrypt data with a symmetric encryption key, then encrypt that key with a public key. Common in systems like envelope encryption.
- Hardware + Software Layers: Combine software encryption with hardware-based encryption, like self-encrypting drives and volume encryption.
- Same vs. Different Algorithms: Use the same algorithm twice or two different ones (e.g., AES and ChaCha20) to reduce shared weaknesses.
- Encryption with Hashing: Add hashing before or after encryption to strengthen integrity and protect stored data like passwords.
- Onion Encryption: Encrypt data in layers for each step through a network. Used in systems like Tor to protect identity and content.
Examples of Double Encryption in Action
Let’s look at a couple of concrete case studies and incidents to see double encryption at work:
Dietrich Law and TitanFile
Dietrich Law, a personal injury firm in Ontario, needed a better way to securely share confidential healthcare documents. Email and couriers caused delays and security concerns.
The firm switched to TitanFile, a PIPEDA-compliant platform that encrypts data in transit and at rest. This gave them two layers of protection without extra steps like password-protecting files.
“TitanFile is flexible, reliable, and has enabled us to send and receive confidential healthcare documents while meeting any concern for security.”
– George Dietrich, Managing Lawyer at Dietrich Law
NSA’s Fishbowl Secure Phone
The NSA built a secure phone using two encryption layers for voice calls—SRTP and IPsec for the network. Each layer used separate keys. This followed the NSA’s “Rule of Two” to keep communication safe even if one layer of security failed.
Double-Encrypted Ransomware Attack
According to Wired, an insurance company was hit by ransomware. After paying, the decryption tool only unlocked one layer. Attackers had encrypted the data twice and demanded a second ransom. This showed that even hackers use double encryption to trap victims twice.
Common Misconceptions About Double Encryption
Double encryption sounds like a strong idea, and in many cases, it is. But it also leads to confusion. Let’s clear up some common myths:
“Double encryption means double security”
Not always. You’re not adding much protection if both layers use the same algorithm with weak keys. The strength comes from independent keys, possibly different algorithms, and good key management, not just doing the same thing twice.
“Why not just use a longer key or a stronger algorithm instead?”
That helps, but it still creates a single point of failure. The data is exposed if the key is stolen or the algorithm is broken. Double encryption reduces that risk by adding an additional layer.
“If I double encrypt, I don’t need to worry about passwords or key management as much”
No matter how many encryption layers you use, the system can crumble if you use weak passwords or mishandle keys. For instance, if both layers use user-chosen passwords and the user chooses the same weak password for both, an attacker might crack that easily (it’s essentially like having two doors with the same cheap lock).
“Double encryption will make performance unbearably slow”
There is indeed a performance cost, but it’s often not as bad as one might fear, especially with modern hardware. Encryption algorithms like AES are high-speed and have CPU support. Two layers of AES might still handle data at hundreds of MB/s throughput on modern processors.
Advantages of Double Encryption
Many organizations use double encryption to boost the security level, meet compliance needs, and reduce risk. Here are the key benefits:
- Stronger Security: Advisors and accountants often exchange large volumes of tax documents, financial reports, and PII. Double encryption ensures client records stay protected, even in a cloud misconfiguration or credential theft.
- Backup Against Algorithm Flaws: Using two different algorithms helps guard against future cryptographic weaknesses or bugs in one system.
- Regulatory Compliance: Helps meet strict compliance standards by showing that even your cloud provider can’t access private data.
- Trusted in Untrusted Environments: Keeps data safe in third-party systems, APIs, or cloud setups where full trust isn’t guaranteed.
- Harder to Crack by Brute Force: Two keys mean double the effort for attackers. It slows them down and increases the resources needed to break in.
- Reduced Risk from Human Error: If one encryption setting is misconfigured, the second layer can still keep the data safe.
- End-User Privacy: When users encrypt data on the client side and re-encrypt it in the cloud, it adds another privacy wall, useful in zero-trust or high-sensitivity setups.
Challenges of Double Encryption
While double encryption brings security benefits, it also introduces several challenges and drawbacks. It’s important to weigh these against the advantages:
Higher CPU Usage and Slower Performance
Double encryption means data is processed twice, once for each layer. This increases CPU load, especially during large file transfers or high-volume operations.
You may also notice higher latency and reduced throughput, which can be a concern for real-time applications like video streaming or voice calls. Modern hardware can handle a lot, but the impact can be noticeable in resource-constrained environments.
More Complex System Design
Running two encryption layers adds extra moving parts. You must ensure both layers work well together, especially if they use different algorithms or operate at different layers (like app-level and disk-level).
Configuration mistakes—like applying the same algorithm twice incorrectly—can weaken security instead of strengthening it. You’ll also need extra testing to ensure everything decrypts correctly without data loss or corruption.
Possible Friction in User Experience
If the encryption process involves the user, like entering two passwords or completing two unlock steps, it can lead to confusion or frustration.
Extra steps can slow down workflows or increase support requests. In security-sensitive environments, users might be okay with the trade-off. Still, in general-use apps or customer-facing tools, too much friction can reduce adoption or lead to insecure workarounds.
But TitanFile abstracts this away. With self-serve access, no training required, and Canadian data residency, legal and regulated firms can deploy industry-leading security without IT bottlenecks.
Double Encryption and Compliance Standards
Encryption is often a key part of meeting compliance requirements in highly regulated industries. Let’s explore how double encryption is viewed under major compliance frameworks like GDPR, HIPAA, and other security policies:
GDPR (General Data Protection Regulation)
GDPR doesn’t require double encryption but calls for “appropriate technical measures” like encryption and pseudonymization.
Article 32 encourages the use of up-to-date security practices. Using two layers of encryption can support claims that your organization follows state-of-the-art data protection.
HIPAA (Health Insurance Portability and Accountability Act)
HIPAA protects health data and requires that covered entities secure patient information. Encryption is listed as “addressable,” meaning it must be used when reasonable.
Double encryption is often adopted in healthcare settings to strengthen defences and demonstrate good faith under the Security Rule.
PCI DSS (Payment Card Industry Data Security Standard)
PCI DSS mandates encryption for cardholder data in transit and at rest. While it doesn’t require double encryption, many systems use layered encryption, such as TLS, for transport and separate encryption within the database. This adds security and can help during audits or breach investigations.
TitanFile goes further by giving clients control over encryption and where their data is stored. For organizations in Canada, TitanFile ensures that all data resides in secure, compliant Canadian data centers, supporting PIPEDA, PHIPA, and provincial privacy laws.
Best Practices for Double Encryption
Below are some key best practices to follow when designing or deploying a multi-layer encryption strategy:
Use Independent, Strong Keys for Each Layer
Never reuse the same key for both layers. Treat Key1 and Key2 as completely separate secrets. Avoid generating Key2 by simply modifying Key1—use different sources or key derivation paths. Depending on the algorithm, stick to recommended key sizes, such as 256-bit keys for AES or 2048+ bits for RSA.
Manage Keys Securely and Separately
Two keys mean double the key management effort. Store them in different environments when possible. For example, use an on-premises HSM for one and a cloud-based KMS for the other. Separate access controls reduce the chance of both keys being compromised at once.
Plan for Performance and Optimize
Double encryption adds overhead. To reduce impact, test where delays might happen. If using multi-core systems, consider encrypting each layer on a separate thread. To keep latency low, you can also explore hardware acceleration for common ciphers like AES.
Thorough Testing and Auditing
Test your setup as a full security system, not just an add-on. Make sure both encryption and decryption work under real-world conditions. Run through edge cases such as:
- What happens if only one key is available?
- Does your system fail safely or lose data?
- Can you recover encrypted data if one environment goes down?
- How does the system behave under high traffic?
- Are error messages leaking any clues?
Simplify Security with TitanFile’s Built-in Encryption
Managing two layers, multiple keys, and compliance standards can quickly become overwhelming. TitanFile eliminates complexity by delivering built-in, dual-layer encryption without added effort for your team.
With TitanFile, your clients can securely upload T4s, bank statements, folders, receipts, and more to a branded portal—all end-to-end encrypted, tracked, and stored in compliance with Canadian privacy laws. We have also been ranked #1 for security in the secure file-sharing category by SecurityScorecard.
Start using TitanFile today and take encryption off your worry list.