Cybersecurity & Data Privacy Blog
Resources to help keep your workplace up to date with cybersecurity and data privacy best practices.
Online Collaboration: A Success Story20130528143528
Online Collaboration: A Success Story
May 28, 2013
3 Steps to a Great Vacation: What not to Share Online20130523140822
How can Secure File Sharing Benefit Manufacturers?20130521141454
How can Secure File Sharing Benefit Manufacturers?
May 21, 2013
How do you Collaborate?20130516144807
How do you Collaborate?
May 16, 2013
Why IT may not be Recommending a SaaS Solution20130514144355
Why IT may not be Recommending a SaaS Solution
May 14, 2013
Could we Live in a Password-free World?20130513153526
Could we Live in a Password-free World?
May 13, 2013
Secure File Sharing and the field of Higher Education20130509153004
Platform Update: New Features20130507080642
Platform Update: New Features
May 7, 2013
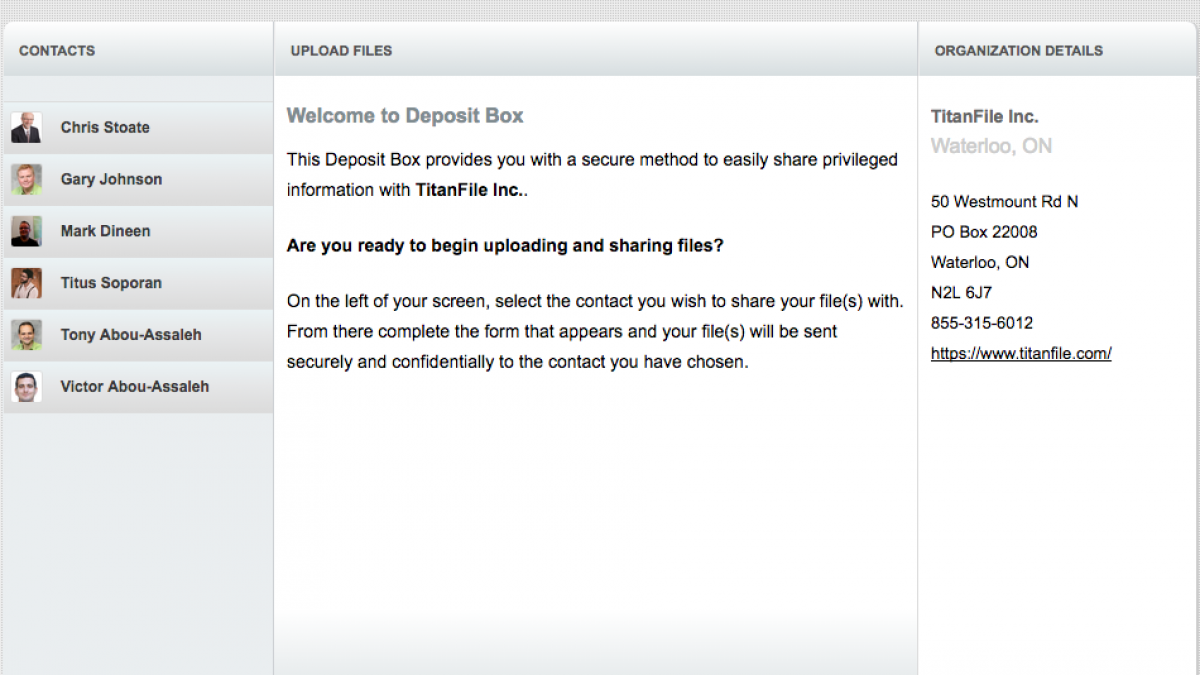
Introducing the TitanFile Secure Deposit Box20130506173135
Introducing the TitanFile Secure Deposit Box
May 6, 2013
Planning for a Worst-case Scenario20130506134730
Planning for a Worst-case Scenario
May 6, 2013
How do you Define Online Privacy?20130502152543
How do you Define Online Privacy?
May 2, 2013
Cybersecurity: A Global Issue20130501125055
Cybersecurity: A Global Issue
May 1, 2013